Methods To Protect Your Cloud Data From Hackers
Cloud is the most secure place to store and retrieve data! No doubt or cross opinion in that yet businesses need to incorporate correct methods and practices to prevent data from hackers. Most cyber-attacks happen for money theft and espionage. It is said that in the year 2019, there are nearly 4 billion records of data breaches. Think how large the count is! By following the correct cloud protection protocols anyone can get rid of this kind of attack.
Why do you need to incorporate cloud protection methods?
First, you need to understand that if something is in cloud alone it does not mean it is safe. Everything on this globe has a definite set of practices and protocols. You need to ensure that the data is shielded to stand against cyber-attacks, theft and corruption. Cyber-attacks are happening even in the big companies like yahoo so businesses should have an absolute concern towards data protection.
Methods to protect cloud data
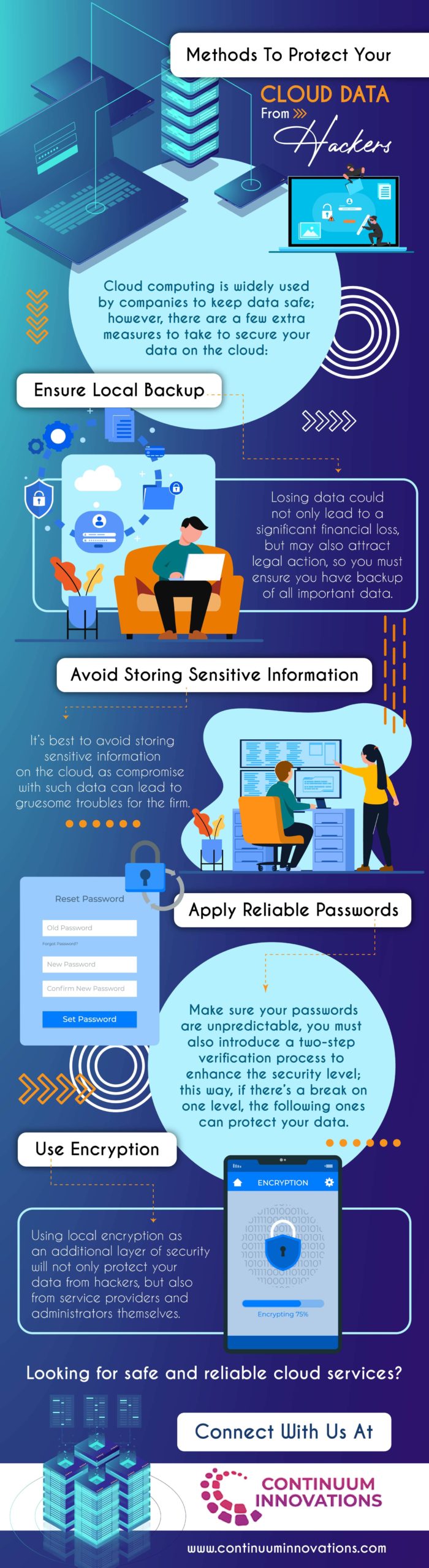
Listed here are some of the methods that need to be followed by organizations to prevent cloud data from hackers.
Data Encryption
Hackers are prevented from accessing your data in the cloud by encryption, which is the conversion of data into secret codes. It is significantly more difficult and takes much longer for hackers to grasp exactly what they are reading since encryption converts your data into ciphertext. With everything in place, only hackers with advanced cryptography abilities would be able to crack the codes in your database. Your data will be protected from hackers and other threats with the additional layer of security provided by data encryption.
Enable right user access
Enabling the right access to the right resource is another important factor in cloud security. Not everyone in the organization needs to access every document. This advice is meant to prevent staff members who lack the necessary skills from unintentionally altering important datasets. It might seem obvious, but many businesses have made the error of having an excessive number of or disorganized permissions, which invariably causes issues.
Be Aware
Lack of awareness is also the prominent reason for cyber-attacks. Statistics state that 95% of human errors paved the possibilities of cyber threats. It is important to be aware in sharing credentials. Inhouse staffs need to log out properly from important tools and websites.
Related Article: Why Businesses need to invest in cloud?
Take time to fix password
Most of the time, we do not make time to create password and go with some of our names, ABCDs and 123s, these are the piece of cake for hackers. A strong password should be at least 12 characters long and contain both capital and lowercase letters, numbers, and symbols. This also applies to encryption, which essentially creates passwords for all of your most important files so that even if a hacker has access to your database, they won’t be able to view specific datasets. You should also enable two-factor verification to add an additional layer of security, making logging in require two steps each time. Another obvious piece of advice is to be careful not to save your passwords on public computers.
Don’t upload highly sensitive data
Of all, viewing all of your data in one location is the whole point of the cloud. However, be cautious to organize it first by removing any of your own personally identifiable information and any confidential information in case there is a breach. Verify that no files containing your passwords or other login information exist so that a hacker cannot simply access the remainder of your data.
Run a Vulnerability test
Establish a routine to check your cloud infrastructure or the SaaS tool hosting your data for weaknesses and easy entry points. This may be requested of you as part of your compliance procedures if your industry is regulated. You may find any holes and weaknesses in your data protection for the cloud security measures by testing them, giving you the chance to fill them before a hacker does.
It would be great to use a SaaS provider or cloud infrastructure provider whose security operations already include vulnerability scans. As a result, your tests add another layer of testing that may find more vulnerabilities.
Pick a right cloud service provider
Half of your job is already done when you have the right cloud managed service provider on your side.
“Some things need to be left out to professionals!” Professional cloud engineers analyze your business requirements and needs and adopt certain methods to prevent your data from hackers. As they will be monitoring your cloud infrastructure round the clock. In case any issues occur, they will identify it and trouble shoot it instantly. They optimize everything from cost to cloud tools.
Cloud professionals update themselves with cloud service providers upgrades. For instance, AWS and Azure keep on adding new features and tools. You may miss out certain insights and tactics if you choose to manage clouds all on your own.
Looking for Managed Cloud Service Providers?
If you are looking for Managed cloud service providers, then you are in the right tab! We continuuminnovations offers optimal solutions and help organizations to store and safeguard their data. Our skilled cloud engineers come up with personalized solutions for all your needs and requirements.
We offer services like