Azure Confidential Computing – Exploring the Ins and Outs
In 2022, Global spending with data security is about 169 billion USD! and it will increase for sure in the succeeding years. The vivid truth is the world does not hesitate to spend money on security. isn’t? Nowadays, data is often encrypted when it is stored or in transition but not when it is in use. i.e., the data in the memory. Microsoft Azure comes in as the rescuer of that data and introduced Confidential computing to encrypt live data. Let’s discover what it is.
What is Azure Confidential Computing?
Confidential Computing is the methodology of providing security to data. It safeguards data in the memory. Confidential computing encrypts data which is in use and decrypts it only when the trusted execution environment (TEE) verifies the cloud environment. It helps to prevent the access of data in various possibilities.
By protecting the data in memory, the organization can isolate their data among other participants while performing combined tasks for machine learning and data analytics. Azure provides a wide range of offerings including services, SDKs and some other tools.
This kind of security protection is much needed for the prominent industries which handles sensitive data like healthcare, Finance and government sectors.
Confidential Computing Consortium
Microsoft has co-founded, Confidential Computing Consortium with a $20 billion investment to democratize confidential computing throughout the globe. Confidential computing consortium (CCC) unites cloud providers, vendors, developers to adopt Trusted Execution Environment (TEE) to provide secured environment to the running data.
Why is it important?
Azure provides you with three big benefits with confidential cloud computing.
Encrypted data in use: Safeguard your data while it is in use. Azure confidential computing decrypts the encrypted data after verifying the cloud environment.
Secure sharing of AI insight: You can upload encrypted data in the shared environment while performing combined tasks so that you can prevent your data accessibility from others.
You own your data: You can retain control of your protected information. With certain tools and solutions, you can customize your own confidential path to access your data.
How does it work?
To understand the working methodology of confidential computing, let’s take a look at the healthcare industry. In the above diagram, there are three columns separated as hospital worker, platform vendor and diagnostics provider.
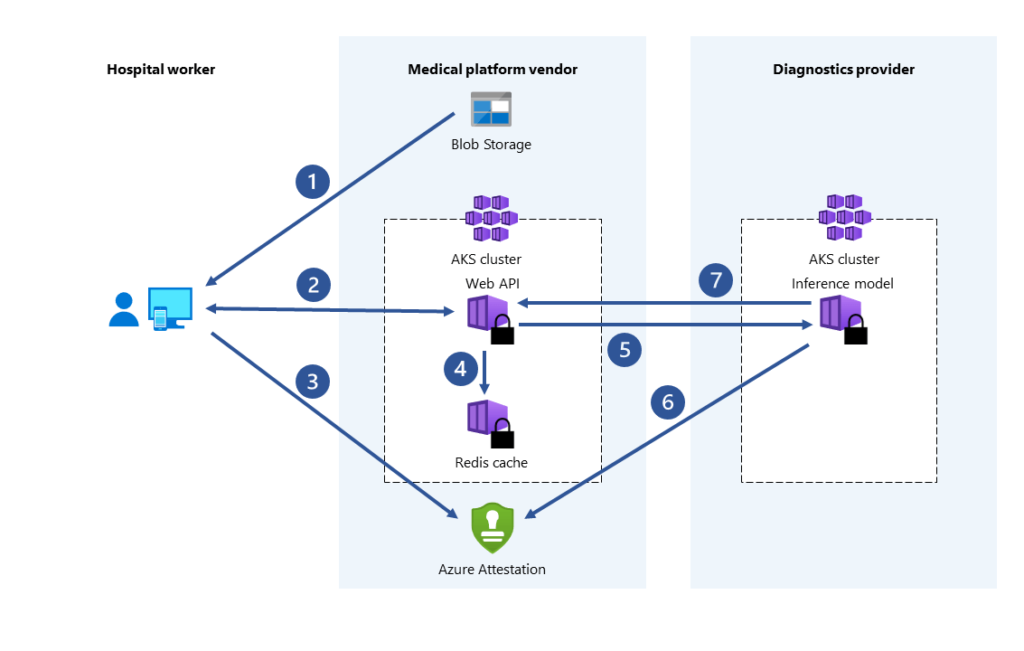
Here is the workflow of confidential computing. With this workflow, we can understand how the data in the memory is encrypted and distributed in the verified cloud environment.
1. Hospital worker enters the data in a web portal which is in Azure Blog Storage
2. That website is linked with a specific API built by some popular medical platform vendor.
3. SCONE, which is in the AKS cluster has enabled Software Guard Extensions (SGX) which helps the containers to run.
4. The API integrated with the hospital’s website verifies the Trusted Execution Environment to decrypt the encrypted data.
5. The client server of the website requests Azure Attestation and gets attestation token from API for verification.
6. Integrated web API additionally requires Reids cache.
7. The web API also has the potential to assist remote services like ML model hosting. While doing such actions it passes attestation token required to evidence the safe environment.
8. The remote infrastructure accepts and verifies the attestation token from API.
9. Then, the diagnostics providers send the data to their run time server.
10. AI model interprets the data and sends it back to the web API app confidentially.
Also Read: Unfolding the insights about Well Architected Review
Use Cases
Security in multi-party computation: At times, an organization needs to collaborate with their partners, vendors or even with multiple parties at those times they do not want to expose their data with them. Azure confidential computing is perfect for such scenarios.
Anti-Money laundering: Multiple banks share their data to run analytics for various purposes. The data contains the transaction details, account number, transaction history, etc. Confidential computing helps the finance sector to prevent their data access. They can also reduce fraud detection rates, data theft and money laundering issues.
Drug Development: Certain drugs are developed by insights derived by Machine Learning. To train ML model, a high volume of healthcare data is required to obtain a quality result. Confidential computing helps at its best to safeguard sensitive medical data.
Data Privacy Assurance: With confidential computing the customer has full access to their hardware and software.
Data Sovereignty: Government store vast amount of sensitive data in the public cloud. Confidential computing is the perfect solution to secure those data. Moreover, it is widely implemented in PaaS in azure.
Bring Your Own Key Scenarios
Secrets being transferred never exist in plaintext outside of an HSM, allowing for scenarios in which keys and certificates are issued and managed by clients while still leveraging cloud-based secure storage.
Blockchain security: Blockchain is a decentralized network with nodes. When it is built on the top of the confidential computing can incorporated hardware-based privacy, data confidentiality and tightened security.
Who We Are?
We, continuum innovations, strive to bring revolution in cloud solutions. We always follow up the footprints of the latest technologies and tactics to give the best service to our clients. Our team has cloud engineers on all the top platforms like AWS, Azure, google, etc. We believe confidential cloud computing is really the superior intervention in the cloud sector. Hope for good!
Our prime service offerings


